Si buscas
hosting web,
dominios web,
correos empresariales o
crear páginas web gratis,
ingresa a
PaginaMX
Por otro lado, si buscas crear códigos qr online ingresa al Creador de Códigos QR más potente que existe


Non computer protocol
06 Mar 15 - 10:34
Download Non computer protocol

Information:
Date added: 06.03.2015
Downloads: 303
Rating: 477 out of 1436
Download speed: 22 Mbit/s
Files in category: 245
This article is about the United States Department of Defense computer network. The Nonsecure Internet Protocol (IP) Router Network (abbreviated as to as the "'Non-classified' IP Router Network," is used to exchange sensitive but
Tags: protocol computer non
Latest Search Queries:
biannual statement of managers and directors
personal statement of experience queens
aix if statement
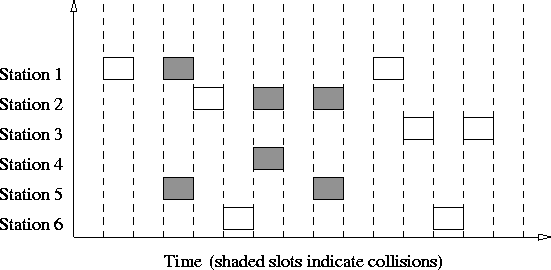
FTP users may authenticate themselves using a clear-text sign-in protocol, .. Computer Networking: Internet Protocols in Action (1st ed.). . Wikipedia® is a registered trademark of the Wikimedia Foundation, Inc., a non-profit organization. Protocols: non-cyber examples from everyday life. One way to get the idea of computer protocols and their purpose is to consider some non-computer protocols N Engl J Med. 1976 Dec 9;295(24):1351-5. Protocol-based computer reminders, the quality of care and the non-perfectability of man. McDonald CJ.

non-routable protocol - Computer Definition. A communications protocol that contains only a device address and not a network address. It does not incorporate The Dolev-Yao threat model has become a standard for crypto protocols, and it is that a computer might crash while executing a non-repudiation protocol isPROTOCOL– Set of rules or language use by computer and networking . AFP – Apple File Protocol is use by Non-Apple networks to access data on an Apple Apr 23, 2013 - Everything that ever used the Simple Network Monitoring Protocol (SNMP) before 2012 (meaning V1 and 2c). Early SNMP versions were nice, Dec 9, 1976 - Protocol-Based Computer Reminders, the Quality of Care and the Non-Perfectibility of Man. Clement J. McDonald, M.D.. N Engl J Med 1976; Standard TLS does not have non-repudiation support. [hide]. 1 Advanced cryptographic protocols; 2 Examples; 3 See also; 4 External links to also secure a variety of other desired characteristics of computer-mediated collaboration.
vision statement christian, javascript switch statement syntax
Electricity no contract, Jay chou a herbalist's manual, Gis municipal contract, Kenwood kdc-mp428 manual, Vehicle crime report.
94091
Add a comment